
Congrats! You have been selected to receive a free luxury cruise trip to the Bahamas! This is an exclusive offer and you have been chosen because of your loyalty to our travel agency. To claim your free cruise trip, simply click HERE. Hurry! This offer is valid for a limited time only and is subject to availability. Don't miss out on this amazing opportunity to experience the vacation of a lifetime!
Ok, you caught me. This isn’t real, there is no free cruise to the Bahamas, and we aren’t even a travel agency. In fact, this isn’t even an email, but chances are you’ve received one like it before. Fraud has been an issue plaguing society since the beginning of civilization. In fact, we got the word “fraud” from the Latin “fraus”, a word used in the Middle Ages to describe criminal deceit. And while Rome may have fallen, the practice of committing fraud continues to live on. In 2021, for example, the Canadian Anti-Fraud Centre reported at least $379 million in reported cyber fraud-related losses.1 As internet service providers, our goal is to try and create a safer and more joyful internet experience by educating others in how to become proficient in identifying and reporting cyber fraud and advocating for safer infrastructure to protect the more vulnerable populations from falling victim to these practices.
After all, the internet should be a happy place, ripe with possibilities and access to equal opportunity. It's important that we all do our part to educate ourselves and others, so let's go deeper into the world of cyber fraud and what to look out for.
Spotting fraud.

To avoid being frauded, it is important to take measures to protect your private information. Even in cases where private data has been compromised (ie. your personal information has been accessed by someone who may want to use it for malicious intent), there are always steps to take to avoid that breach from being used against you. For example, the act of identity theft is simply having your personal information taken while the act of identity fraud is when someone actively uses your personal information to commit a crime. So you can see why fraud prevention starts first with arming yourself with the knowledge on how to protect your private information online.
The obvious and the not so obvious.
The Canadian Anti-Fraud Centre reported that identity fraud was the most common type of fraud, with a whopping 30,849 people reporting this crime in 2021 alone. Most of us with a phone have likely received a call from an unknown number claiming to be a representative from Amazon who is concerned about your purchase of the latest iPhone or perhaps even the RCMP letting you know that there is a warrant out for your arrest. If you’ve never received a call like this before, you can’t be faulted for believing your Amazon account (or innocence) has been compromised.
Over SMS or email, it is often easier to tell when someone is trying to scam you. Oftentimes, these messages are riddled with typos and a quick reverse google search of the number or email address will show you it is not associated with the actual institution it claims to be. For example, here’s an email I received from “T-Mobile” telling me that my recent purchase (never happened) resulted in me winning a $100 prize. As you can see, Gmail already flagged this email as spam so I had never even seen it until I went dumpster-diving in my spam folder. Furthermore, the email address it originated from is clearly not one associated with T-Mobile. That paired with the awkwardly placed punctuation and questionable grammar was evidence enough that I was sadly not about to be the recipient of $100.
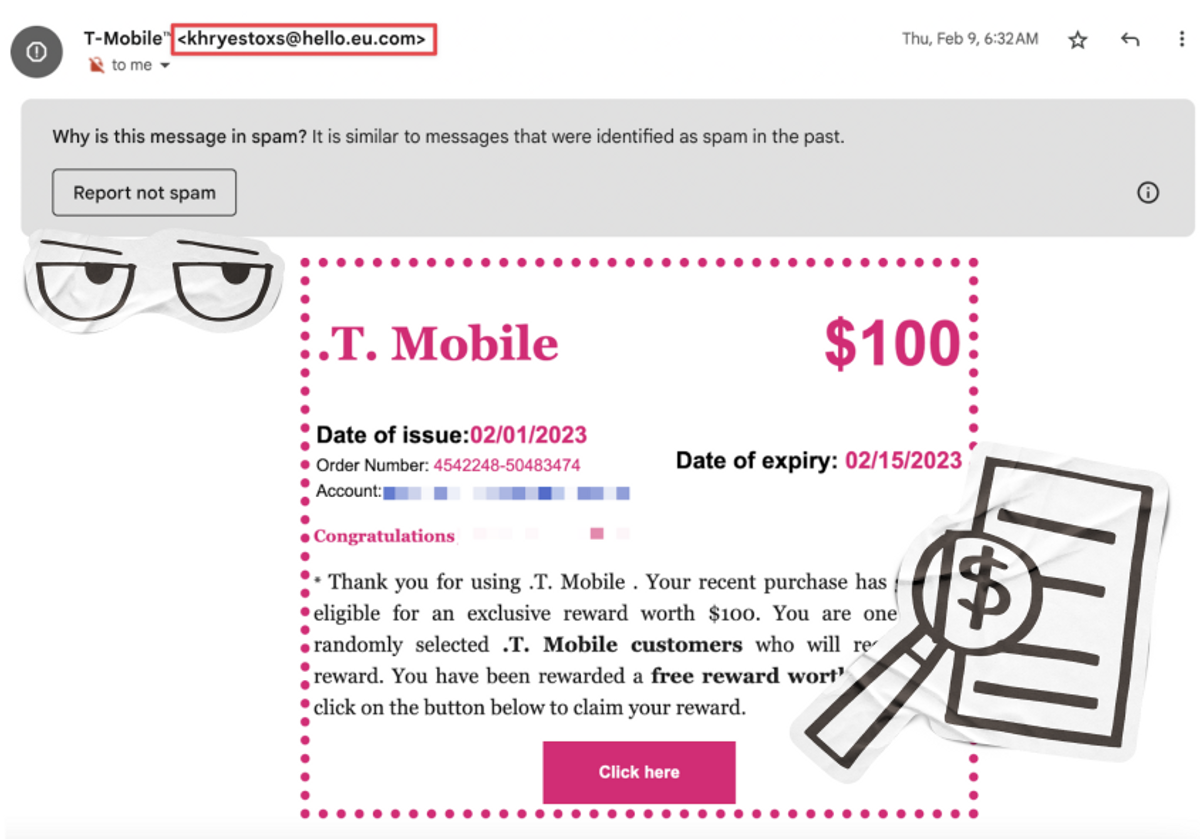
That being said, sometimes emails like this can be convincing, such as when fraudsters created an entire fake website that looked nearly identical to PayPal’s and began sending people links to log in to accept a pending payment.2 This is what is broadly known as a phishing scam, a method fraudsters utilize frequently for how easy it can be to collect someone’s private information for nefarious purposes–all it takes sometimes is someone’s click of a button.
Phishing (or: fishing for sensitive information).
A phishing scam is any sort of communication wherein the goal is for the recipient to click on a link and provide personal information. Sometimes, the goal itself is just to have the link clicked so that malware can be installed on your device and from there, the fraudsters can collect what they need via various spyware. An example of this can be seen in the 2018 heist movie Ocean’s 8 where NineBall (played by Rihanna) sends an employee of a security company a link to a fake website she created dedicated to photos of his favourite dog breed of which he has an undying devotion towards. The man simply can’t resist and within seconds, NineBall has complete access and control over his work computer which she uses to then gain access to the security system at the Metropolitan Museum of Art (Guess she really didn’t want to pay the $30 admission fee).

To put it simply, a weakness was found (the employee’s love of Wheaten Terriers) and then exploited. A lot of phishing scams are exactly this, preying on the desire of those to either a) gain money or b) prevent the loss of money. This is why scam emails often have a lot of urgency to them, providing timers until when you can claim your prize or telling you to act quickly to prevent monetary loss. In actuality, companies like Amazon, PayPal, and even oxio will never require you to provide sensitive information such as your credit card information via SMS or email. A good rule of thumb is to always double check the email address of the sender by going directly to the company’s website and logging into your account to view any recent activity or reaching out to the support team to confirm the validity of the email.
I think I've been compromised. What's next?
Let’s say, despite being cautious, you accidentally click a link you believe is a phishing link (oops). In fact, let’s take it a step further and say you entered sensitive information such as your email and password and possibly even your credit card information. It’s normal to panic in such a situation, but it’s also not the end of the world. Here are a few example scenarios and what the suggested steps are to protect yourself after the fact.
I clicked on a suspicious link but didn't give them any details.
Just to be safe, as clicking on a link can install malware on a device (as was the case with the Ocean’s 8 example), disconnect the device from the wifi network as soon as you can to prevent any malware from moving via the network to other devices connected to it. Once this is done, backup all your important files on a USB as this does not require a network connection and then run a scan of your device for any malware. To be safe, running this scan on all your devices that were on the wifi network is the best bet. This last part may be the hardest step as it isn’t exactly common knowledge on how to run an in-depth malware scan. For this, go to a professional.
Oh, and don’t forget, change your passwords!
I clicked on a suspicious link and provided personal information.
The above steps still apply here but now there is the added step of fixing or preventing any criminal activity the fraudsters may now attempt with your personal information. For example, if credit card information was provided, call your bank immediately to report the incident and put a lock on your card. Or, if you provided log-in credentials to a website, contact their support immediately and, if you are still logged into your account, change the password right away. As a courtesy to protect your friends and family, let them know your account was compromised as it’s common for hackers to try and target them too, as many people will not question opening a link that was sent to them by someone they trust. Unless it’s your weird uncle whose Facebook posts you typically ignore anyway.
To take preventative measures, 2-Factor Authentication (2FA) is a setting that can be enabled for many social media sites such as Facebook or Twitter. This is a security process that prompts you to use two different forms of identification in order to access your online account. For example, it may ask you for a pin or code that goes to a separate device, such as your phone. It may be a good idea to turn this setting on to make your account even more secure.
Why does an ISP care about fraud prevention anyway?
By now, you may be wondering why an ISP is invested in protecting your internet safety. And even if you weren’t wondering, I’ll tell you anyway. First and foremost, we provide a service and we want that service to be enjoyable, whether it’s through consistent speeds, a stable connection, through our customer support or, in this case, spreading awareness to keep you and your loved ones safe from online attacks.
There are already some things we offer on our end to try and minimize the risk for those that use our services. For example, customers are able to opt for eero Plus which provides additional router security features such as anti-malware software, encrypted VPN, ad-blocking, and much more.3
On the infrastructure level, we also take steps in trying to keep our customers safe from cybersecurity threats, such as the blocking of certain ports and inbound traffic. For example, SMTP (Simple Message Transfer Protocol) is a protocol used for sending and receiving emails over the internet.4 The reason we block this port goes back to the phishing schemes mentioned earlier. Let’s say you click on one and unknowingly have malware installed on your device, which then infects your network. If your SMTP is open, the virus or malware can then easily convert your device into an SMTP relay and use it to spread hundreds of thousands of phishing links to other users.
SMTP ports can even be targeted for something called distributed denial-of-service (DDoS) attacks, where multiple devices send requests to overwhelm a server, which then causes it to crash. Not too long ago, a 15-year old kid who went by Mafiaboy did exactly this to multiple e-commerce sites like eBay, Amazon, and even the search engine Yahoo.5 This DDoS attack rendered Yahoo useless for almost an entire hour and for a large company such as Yahoo, being inaccessible for an hour is quite a big deal! For this reason, oxio as well as other ISPs block this particular port from being open, although you can still safely send and receive emails on your network.
And while there are many things we can do and provide as an ISP to reduce cybersecurity threats on our network, being educated on how to spot and prevent fraud before it happens can create a safer internet for everyone.
Thanks Danilo, Savannah, and Shion for all the feedback and support as always. Thanks as well to Matthieu Louis for providing his technical expertise!








